Abstract
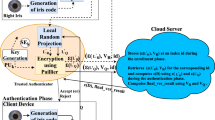
Homomorphic Encryption (HE) is the most widely explored research area to construct privacy-preserving biometric authentication systems due to its advantages over cancelable biometrics and biometric cryptosystem. However, most of the existing privacy-preserving biometric authentication systems using HE assume that the server performs computations honestly. In a malicious server setting, the server may return an arbitrary result to save the computational resources results in false accept/reject. To address this, we propose a privacy-preserving and verifiable multi-instance iris authentication using public auditor (PviaPA). Paillier HE provides confidentiality for the iris templates in PviaPA. A public auditor ensures the correctness of comparator result in PviaPA. Extensive experimental results on benchmark iris databases demonstrate that PviaPA provides privacy to the iris templates with no loss in the accuracy as well as trust on the comparator result.






Similar content being viewed by others
References
Ross AA, Nandakumar K, Jain AK (2006) Handbook of multibiometrics: human recognition systems, vol 6. Springer
Jain AK, Flynn P, Ross AA (2007) Handbook of biometrics. Springer Science & Business Media
Saini R, Rana N (2014) Comparison of various biometric methods. Int J Adv Sci Technol 2(1):24–30
Daugman J (January 2004) How iris recognition works. IEEE Trans Cir Sys Video Technol 14(1):21–30. https://doi.org/10.1109/TCSVT.2003.818350
Prabhakar S, Pankanti S, Jain AK (2003) Biometric recognition: Security and privacy concerns. IEEE Secur Privacy 1(2):33–42
Maiorana E, Hine GE, Campisi P (2014) Hill-climbing attacks on multibiometrics recognition systems. IEEE Trans Inf Forensic Secur 10(5):900–915
Venugopalan S, Savvides M (2011) How to generate spoofed irises from an iris code template. IEEE Trans Inf Forensic Secur 6(2):385–395
Jain AK, Nandakumar K, Nagar A (2008) Biometric template security. EURASIP J Adv Signal Process 2008(113):1–17
Rathgeb C, Uhl A (2011) A survey on biometric cryptosystems and cancelable biometrics. EURASIP J Inf Secur 2011(1):1–25
Ignatenko T, Willems Frans MJ (2010) Information leakage in fuzzy commitment schemes. IEEE Trans Inf Forensic Secur 5(2):337–348
Fontaine C, Galand F (2007) A survey of homomorphic encryption for nonspecialists. EURASIP J Inf Secur 2007(1):15–25
Upmanyu M, Namboodiri AM, Srinathan K, Jawahar CV (2010) Blind authentication: a secure crypto-biometric verification protocol. IEEE Trans Inf Forensic Secur 5(2):255–268
Troncoso-Pastoriza JR, González-Jiménez D, Pérez-González F (2013) Fully private noninteractive face verification. IEEE Trans Inf Forensic Secur 8(7):1101–1114
Simoens K, Bringer J, Chabanne H, Seys S (2012) A framework for analyzing template security and privacy in biometric authentication systems. IEEE Trans Inf Forensic Secur 7(2):833–841
Gasti P, Šeděnka J, Yang Q, Zhou G, Balagani K S (2016) Secure, fast, and energy-efficient outsourced authentication for smartphones. IEEE Trans Information Forensic Secur 11(11):2556–2571
Abidin A, Aly A, Rúa EA, Mitrokotsa A (2016) Efficient verifiable computation of xor for biometric authentication. In: International Conference on Cryptology and Network Security. Springer, pp 284–298
Gomez-Barrero M, Maiorana E, Galbally J, Campisi P, Fierrez J (2017) Multi-biometric template protection based on homomorphic encryption. Pattern Recogn 67:149–163
Zhou K, Ren J (2018) Passbio: Privacy-preserving user-centric biometric authentication. IEEE Trans Inf Forensic Secur 13(12):3050–3063
Hu S, Li M, Wang Q, Chow SSM, Du M (2018) Outsourced biometric identification with privacy. IEEE Trans Inf Forensic Secur 13(10):2448–2463
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes. In: International conference on the theory and applications of cryptographic techniques. Springer, pp 223–238
Osadchy M, Pinkas B, Jarrous A, Moskovich B (2010) Scifi-a system for secure face identification. In: 2010 IEEE Symposium on Security and Privacy. IEEE, pp 239–254
Rahulamathavan Y, Phan R C-W, Chambers JA, Parish DJ (2012) Facial expression recognition in the encrypted domain based on local fisher discriminant analysis. IEEE Trans Affect Comput 4(1):83–92
Šeděnka J, Govindarajan S, Gasti P, Balagani KS (2014) Secure outsourced biometric authentication with performance evaluation on smartphones. IEEE Trans Inf Forensic Secur 10(2):384–396
Penn G M, Pötzelsberger G, Rohde M, Uhl A (2014) Customisation of paillier homomorphic encryption for efficient binary biometric feature vector matching. In: 2014 International Conference of the Biometrics Special Interest Group (BIOSIG). IEEE, pp 1–6
Haghighat M, Zonouz S, Abdel-Mottaleb M (2015) Cloudid: Trustworthy cloud-based and cross-enterprise biometric identification. Expert Syst Appl 42(21):7905–7916
Yasuda M, Shimoyama T, Kogure J, Yokoyama K, Koshiba T (2015) New packing method in somewhat homomorphic encryption and its applications. Secur Commun Netw 8(13):2194–2213
Xiang C, Tang C, Cai Y, Xu Q (2016) Privacy-preserving face recognition with outsourced computation. Soft Comput 20(9):3735–3744
Hahn C, Hur J (2016) Efficient and privacy-preserving biometric identification in cloud. ICT Express 2(3):135–139
Kumar S, Singh SK, Singh AK, Tiwari S, Singh RS (2018) Privacy preserving security using biometrics in cloud computing. Multimed Tools Appl 77(9):11017–11039
Taheri M, Mozaffari S, Keshavarzi P (2018) Face authentication in encrypted domain based on correlation filters. Multimed Tools Appl 77(13):17043–17067
Boddeti VN (2018) Secure face matching using fully homomorphic encryption. In: 2018 IEEE 9th International Conference on Biometrics Theory, Applications and Systems (BTAS). IEEE, pp 1–10
Fan J, Vercauteren F (2012) Somewhat practical fully homomorphic encryption. IACR Cryptol ePrint Arch 2012:1–19
Zhu H, Wei Q, Yang X, Lu R, Li H (2018) Efficient and privacy-preserving online fingerprint authentication scheme over outsourced data. IEEE Trans Cloud Comput:1–11
Lee J, Kim D, Kim D, Song Y, Shin J, Cheon JH (2018) Instant privacy-preserving biometric authentication for hamming distance. IACR Cryptol ePrint Arch 2018:1214–1242
Barni M, Droandi G, Lazzeretti R, Pignata T (2019) Semba: secure multi-biometric authentication. IET Biom 8(6):411–421
Guo S, Xiang T, Li X (2019) Towards efficient privacy-preserving face recognition in the cloud. Signal Process 164:320–328
Topcu B, Erdogan H (2019) Fixed-length asymmetric binary hashing for fingerprint verification through gmm-svm based representations. Pattern Recogn 88:409–420
Rathgeb C, Uhl A, Wild P, Hofbauer H (2016) Design decisions for an iris recognition sdk. In: Handbook of iris recognition. Springer, pp 359–396
Wang Y, Yao H, Zhao S (2016) Auto-encoder based dimensionality reduction. Neurocomputing 184:232–242
24745:2011 (2018) Iso/iec 24745:2011 - information technology – security techniques – biometric information protection. https://www.iso.org/standard/52946.html
Yin Y, Liu L, Sun X (2011) Sdumla-hmt: a multimodal biometric database. In: Chinese Conference on Biometric Recognition. Springer, pp 260–268
Kumar A, Passi A (2010) Comparison and combination of iris matchers for reliable personal authentication. Pattern Recogn 43(3):1016–1026
Martinez-Diaz M, Fierrez-Aguilar J, Alonso-Fernandez F, Ortega-García J, Siguenza JA (2006) Hill-climbing and brute-force attacks on biometric systems: A case study in match-on-card fingerprint verification. In: Proceedings 40th Annual 2006 International Carnahan Conference on Security Technology. IEEE, pp 151–159
Hadid A, Evans N, Marcel S, Fierrez J (2015) Biometrics systems under spoofing attack: an evaluation methodology and lessons learned. IEEE Signal Proc Mag 32(5):20–30
Punithavathi P, Geetha S, Sasikala S (2017) Generation of cancelable iris template using bi-level transformation. In: Proceedings of the 6th International Conference on Bioinformatics and Biomedical Science, pp 94–100
Gomez-Barrero M, Rathgeb C, Li G, Ramachandra R, Galbally J, Busch C (2018) Multi-biometric template protection based on bloom filters. Inf Fusion 42:37–50
Sadhya D, Raman B (2019) Generation of cancelable iris templates via randomized bit sampling. IEEE Trans Inf Forensic Secur 14(11):2972–2986
Morampudi MK, Prasad Munaga VNK, Raju USN (2020) Privacy-preserving iris authentication using fully homomorphic encryption. Multimed Tools Appl:1–23
Kumar M M, Prasad MVNK, Raju USN (2020) Bmiae: Blockchain-based multi-instance iris authentication using additive elgamal homomorphic encryption. IET Biom 9(4):165–177
Dwivedi R, Dey S, Singh R, Prasad A (2017) A privacy-preserving cancelable iris template generation scheme using decimal encoding and look-up table mapping. Comput Secur 65:373–386
Lai Y-L, Jin Z, Teoh ABJ, Goi B-M, Yap W-S, Chai T-Y, Rathgeb C (2017) Cancellable iris template generation based on indexing-first-one hashing. Pattern Recogn 64:105–117
Soliman RF, Amin M, Abd El-Samie FE (2020) Cancelable iris recognition system based on comb filter. Multimedi Tools Appl 79(3):2521–2541
Gad R, Talha M, Abd El-Latif A A, Zorkany M, Ayman EL-S, Nawal EL-F, Muhammad G (2018) Iris recognition using multi-algorithmic approaches for cognitive internet of things (ciot) framework. Futur Gener Comput Syst 89:178–191
Kamlaskar C, Deshmukh S, Gosavi S, Abhyankar A (2019) Novel canonical correlation analysis based feature level fusion algorithm for multimodal recognition in biometric sensor systems. Sens Lett 17 (1):75–86
Walia GS, Rishi S, Asthana R, Kumar A, Gupta A (2019) Secure multimodal biometric system based on diffused graphs and optimal score fusion. IET Biom 8(4):231–242
Hinton GE, Salakhutdinov RR (2006) Reducing the dimensionality of data with neural networks. Science 313(5786):504–507
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix
1.1 A Preliminaries
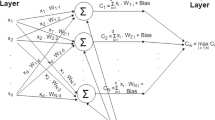
Autoencoder Autoencoder is an unsupervised neural network method. It optimizes a rebuilding of the input data in the output layer through a hidden layer with chosen dimensions. The input, hidden, and output are the layers present in the autoencoder. The dimensions of output and input layers are the same, whereas the hidden layer contains fewer dimensions. Autoencoder consists of two phases, 1) encoder and 2) decoder. An encoder converts the input data into a hidden code, and the decoder reconstructs the original input data from the hidden code. The input and output for an autoencoder are I∈ [0, 1]d and O∈ [0, 1]d, where d is the number of dimensions. Firstly, the encoder maps the input into hidden (or) latent code, h∈ \([0, \ 1]^{d^{\prime }}\), \(d^{\prime }\) < d using the transformation given in (10).
Where S is a sigmoid function, W is a weight matrix, and b is the bias. The hidden code, h is then converted back into O with the same dimension as I by using the decoder. The conversion occurs through the transformation given in (11).
Where S is a sigmoid function, \(W^{\prime }\) is a weight matrix of the reverse mapping, and b is the bias. The average reconstruction error is maximized by optimizing the parameters (\(W,\ b, \ b^{\prime }\)). The reconstruction error can be measured by either squared error, L(I,O) = ||I − O||2 or binary cross-entropy, \(L(I, \ O) \ = \ - {\sum }_{k=1}^{d}[I_{k}log O_{k} + (1 - I_{k}) log(1-O_{k})]\). Similar to the state-of-the-art dimensionality reduction techniques such as linear discriminant analysis (LDA), principal component analysis (PCA), isometric mapping (ISOMAP), etc. autoencoder can be used to reduce the high-dimensional feature vector [56]. To use the autoencoder as a dimensionality reduction technique, use the data obtained in hidden layer and discard the decoder phase.
B Algorithms to generate encrypted verification vector and check the correctness of Manhattan distance
1.1 B.1 Generation of encrypted verification vector
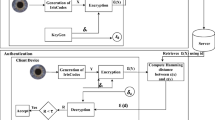
The TA implements the Algorithm 3 after the enrollment phase. The verification vector denoted as Zn+ 1 is initialized to (1, 1, ..., 1). Zn+ 1 and Xi are of same dimensions. Encrypt Zn+ 1 using the public key Pk. The function randomInteger() generates a random value vi. Encrypt vi using the public key Pk. The random value generated in each and every iteration is encrypted with different public keys. The keys used to encrypt vi are completely different from the keys used to encrypt iris templates. multiply function is used to achieve the property 1 of Paillier discussed in Section 3.3. The function multiply is called to perform the multiplication between jth value of ε(Xi) and ε(vi), where i varies from 1 to N. ε(tmp) stores the multiplication result. The function multiply is called to perform the multiplication between ε(Zn+ 1) and ε(tmp). After the completion of m iterations, ε(Zn+ 1) which is shown in (8) is obtained. The N random values are assigned to ε(V ). The TA sends ε(Zn+ 1) and ε(V ) to the PA after all the users are enrolled.

B.2 Ensuring the correctness of Manhattan distance
The steps (4-8) of Algorithm 4 computes \(\varepsilon (D1) = {\prod }_{j=1}^{m}(\varepsilon (Z_{n+1}[j]) \cdot \varepsilon (Y[j]))\). The steps (11-15) of Algorithm 4 computes \(\varepsilon (D2)={\prod }_{i=1}^{N}(\varepsilon (r_{i}) \cdot \varepsilon (v_{i}))\). The PA decrypt ε(D1) and ε(D2). Finally, compute ε(D1) − ε(D2) and send the result to TA. If the result is zero, the Manhattan distances ε(R) returned by the CS are considered to be correct. So, the TA finds the value with index id given by the end-user. The value is compared with a threshold, τ to determine whether the user is valid or not.

Rights and permissions
About this article
Cite this article
Morampudi, M.K., Prasad, M.V.N.K. & Raju, U.S.N. Privacy-preserving and verifiable multi-instance iris remote authentication using public auditor. Appl Intell 51, 6823–6836 (2021). https://doi.org/10.1007/s10489-021-02187-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-021-02187-8